BQT Biometrics Australia: Blazing A Trail in Biometric Protection Modern Technology
The Future of Safety And Security: Discovering the current Trends in Electronic Safety Technologies
In the realm of security and safety, the landscape is regularly advancing, driven by technical advancements that press the borders of what is feasible. Electronic safety innovations have ended up being significantly sophisticated, offering cutting-edge solutions to address the ever-growing challenges dealt with by people and companies alike. From biometric verification to the integration of expert system and equipment knowing, these fads hold the guarantee of boosting safety procedures in unprecedented means. As we navigate with this detailed web of innovations, one can not aid but wonder exactly how these modern technologies will shape the future of security and safety and security, establishing the phase for a brand-new age of defense and strength (BQT Solutions).
Surge of Biometric Verification
With the enhancing demand for secure and hassle-free authentication methods, the surge of biometric authentication has actually transformed the way individuals gain access to and shield their delicate info. Biometric verification utilizes distinct organic characteristics such as fingerprints, face functions, iris patterns, voice recognition, and also behavioral characteristics for identification verification. This innovation supplies an extra trustworthy and protected technique contrasted to conventional passwords or PINs, as biometric data is unbelievably challenging to reproduce or take.
Among the crucial benefits of biometric verification is its comfort. Customers no longer require to bear in mind complicated passwords or stress regarding shedding access as a result of neglected credentials. By merely making use of a part of their body for confirmation, people can promptly and securely access their gadgets, accounts, or physical rooms.
In addition, biometric verification improves safety and security by providing a much more durable defense versus unapproved accessibility. With biometric markers being special to each individual, the danger of identity burglary or unapproved entrance is significantly minimized. This enhanced level of safety and security is especially vital in markets such as financing, health care, and federal government where shielding delicate info is critical.
Assimilation of AI and Artificial Intelligence
The development of electronic safety and security technologies, exemplified by the increase of biometric verification, has actually paved the means for improvements in the integration of AI and Machine Discovering for boosted identification and defense systems. By leveraging AI formulas and Maker Learning versions, digital protection systems can currently evaluate large amounts of information to find patterns, abnormalities, and possible risks in real-time. These technologies can adapt to progressing security dangers and offer aggressive reactions to alleviate dangers effectively.
One substantial application of AI and Device Knowing in electronic safety and security remains in predictive analytics, where historic data is used to anticipate prospective protection violations or cyber-attacks. This proactive strategy allows protection systems to expect and protect against risks before they happen, enhancing total safety procedures. In addition, AI-powered security systems can intelligently check and analyze video clip feeds to recognize suspicious activities or people, boosting action times and lowering false alarms.
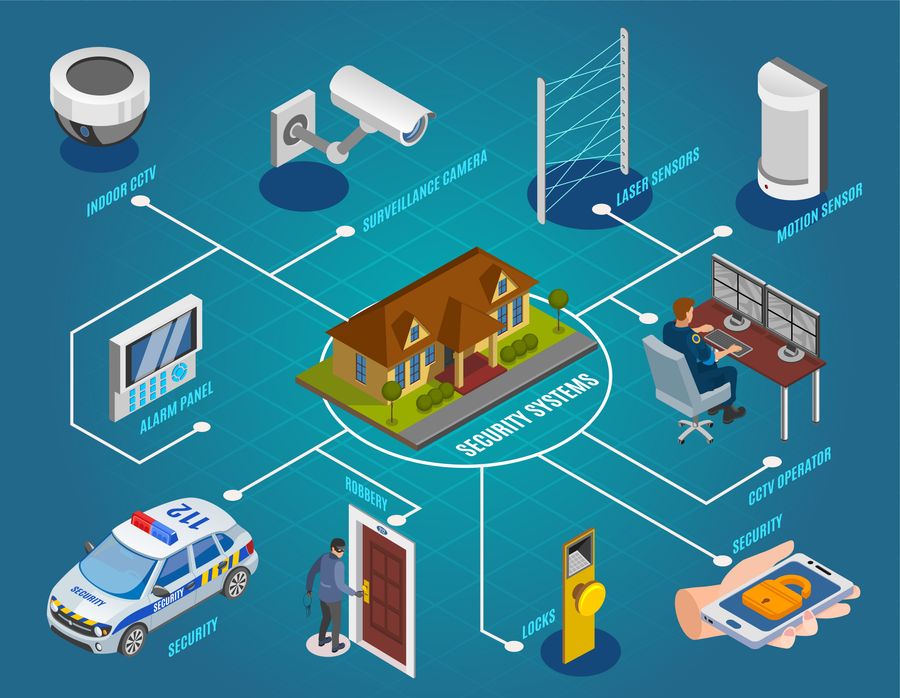
IoT and Smart Protection Tools
Advancements in electronic protection modern technologies have brought about the emergence of IoT and Smart Security Gadgets, changing the way security systems run. The Web of Things (IoT) has actually allowed safety devices to be interconnected and from another location obtainable, using boosted surveillance and control capabilities. Smart Security Tools, such as smart cams, door locks, and movement sensing units, are geared up with capabilities like real-time signals, two-way communication, and combination with other smart home systems.
Among the substantial advantages of IoT and Smart Safety Gadgets is the here are the findings ability to supply individuals with seamless access to their safety and security systems with smartphones or other internet-connected devices. This comfort permits for remote surveillance, equipping, and disarming of safety and security systems from anywhere, supplying property owners with assurance and adaptability. These tools frequently integrate sophisticated functions like face acknowledgment, geofencing, and activity pattern recognition to improve total safety and security degrees.
As IoT remains to evolve, the combination of expert system and machine knowing algorithms right into Smart Security Tools is expected to additional boost detection accuracy and modification alternatives, making electronic safety and security systems also more reliable and reliable.
Cloud-Based Safety Solutions
Emerging as a crucial element of modern digital security framework, Cloud-Based Safety and security Solutions provide exceptional flexibility and scalability in guarding digital properties. Cloud-based safety solutions enable remote surveillance, real-time notifies, and centralized monitoring of safety and security systems from any type of location with a web link.
In addition, cloud-based safety services supply automatic software program updates and upkeep, ensuring that safety systems are constantly updated with the current defenses versus arising dangers. The scalability of cloud-based remedies permits companies to quickly increase their security facilities as required, accommodating growth and adjustments in security demands. Furthermore, cloud-based protection solutions typically feature built-in redundancy and catastrophe healing abilities, minimizing the danger of information loss or system downtime. On the whole, cloud-based security solutions represent an economical and reliable means for organizations to boost their security position and secure their electronic assets.
Focus on Cybersecurity Procedures
With the increasing sophistication of cyber dangers, companies are placing an extremely important concentrate on reinforcing their cybersecurity actions. BQT Sideload locks. As technology breakthroughs, so do the techniques used by cybercriminals to breach systems and take sensitive info. This has motivated organizations to spend heavily in cybersecurity actions to safeguard their information, networks, and systems from harmful strikes
One of the vital patterns in cybersecurity is the fostering of sophisticated security procedures to guard data both at remainder and in transit. Security helps to make certain that also if information great post to read is intercepted, it continues to be unreadable and secure. In addition, the implementation of multi-factor verification has come to be progressively usual to add an additional layer of safety and security and confirm the identifications of users accessing sensitive info.

Conclusion